“My computer got infected! How is that even possible? I don’t even visit any naughty sites!”
There are a number of ways your computer can get infected. It doesn’t just have to do with what websites you visit – no matter how clean they appear to be. Every website we browse in this day and age has code embedded in it. It is also possible that within that embedded code is another section with more embedded code. Code-ception. Code inside of code inside of code… possibly inside of more code. All it takes is for a hacker to embed his virus in an advertisement or image. It doesn’t even have to be a part of the actual website. In a basic sense ads are embedded images on webpages, they are an image you are seeing from an entirely different source than the webpage you are visiting.
What I’m getting at here is the advertisement you see on CNN’s webpage isn’t actually loading from cnn.com, but from another host altogether. CNN might not be directly compromised, but the advertising firm hosting their ads could be. It also makes more sense for hackers to use these ad hosts as it allows them to target a much larger network of victims. You might visit a webpage which displays a particular advertisement or image and your computer will download the image due to web browsers “caching” common items. This common practice is what allows for webpages to load quickly after you’ve already visited them once before.
Now obviously this isn’t the only way you can get infected, but this is a prime example of how easy it is to get infected even when practicing safe browsing habits. Everything is working as intended and that is exactly how hackers exploit these systems to infect you. They prey on calculated computer and human behavior. That’s why some people end up infecting themselves through pop-ups.
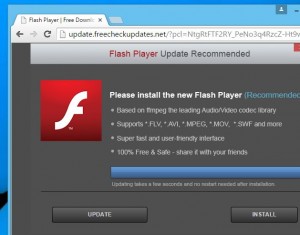
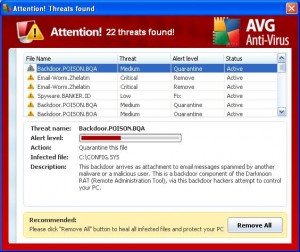
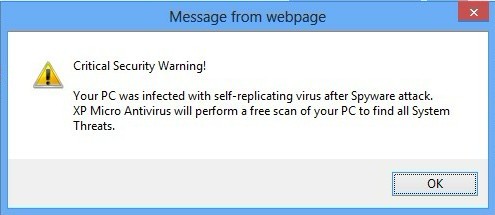
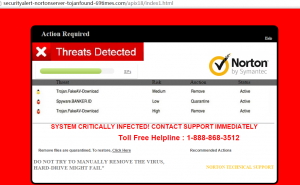
You can be browsing on a website you normally use and all of the sudden you’re hit with a wave of pop-up advertisements – except they look incredibly similar to your anti-virus program or other programs you normally use. At a quick glance you think the program is just trying to remind you to scan your computer or update so you click on it just to get it out of your way. This is where you’ve unfortunately made a dire mistake that many people make. That one misclick to accept that prompt now has your computer infected with a virus! This is just one of many reasons why I recommend Ad Blocking extensions, but that’s an entirely different beast for another article. Here are a few examples of what those pop-ups may look like.
Don’t worry, these are safe to click on.
You can get infected in a similar manner by opening e-mails that contain malicious code in Outlook or other e-mail programs. I know many people love to use an offline e-mail program, but the truth is that web based e-mail is far safer as every e-mail remains on the external server unless you choose to download it to your hard disk. The hosting company of that external server has its own security measures in place, thus further reducing the chance that you will download an infected file attached to your e-mail.
You almost have to deliberately try to download a virus in this fashion as it will look out of place. Never download anything that you do not recognize. I’ve had customers admit they innocently downloaded an unrecognized file from an e-mail because they were under the impression they could trust the sender.
My last piece of advice in this section to avoid getting infected is to watch what you download. Learn common file extensions and make sure that when you are downloading a document that it is actually the corresponding document extension. If it’s a word document, make sure it ends with .doc. If it is an excel document make sure it ends with .xls. I’ve seen people try to download a document they believe is legitimate except it ends in .exe – this is an executable file.
When you open an .exe it executes a script of code (typically to install a program). Hackers upload malicious .exe’s to popular file hosting websites in hopes that people are naive enough to download and run them. Another trick they use is creating look-alike websites in hopes that you won’t notice the URL in your address bar has the website you are really looking for vaguely misspelled. You can see examples of this in two of the images I posted above.
In part 3 you can read about why your anti-virus program may not catch all the threats you face on the Internet as well as find the proper utilities and some methods you can use to disinfect your computer system.